I tend to have a look at the profiles following me on Twitter or trying to connect on LinkedIn. On LinkedIn I’ve become a little picky on whom to connect with and they have to match my career interests. On Twitter I just look for red flags in general. If your profile promotes racism and hate speech, deliberately spreads disinformation or supports Borussia Dortmund, I will block you (just kidding on the last one). Of course, I can’t do a deep dive into each and every follower on Twitter. But today I would like to show you what kind of red flags I look for and how these can lead to further investigations.
Follow me and I’ll check out your profile
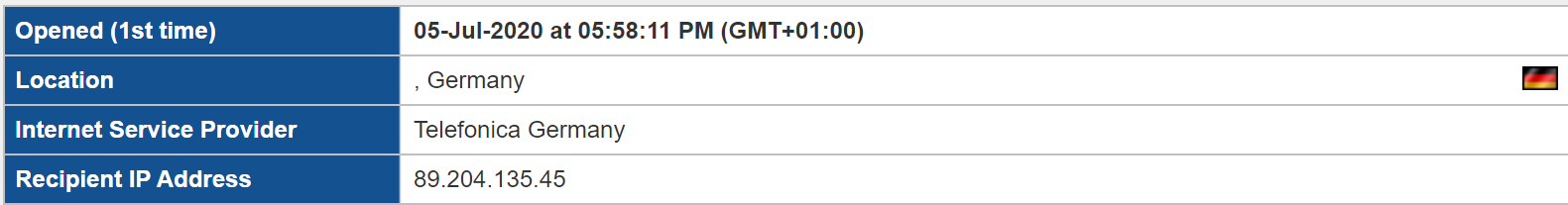
Around lunch time I noticed a new follower on Twitter.

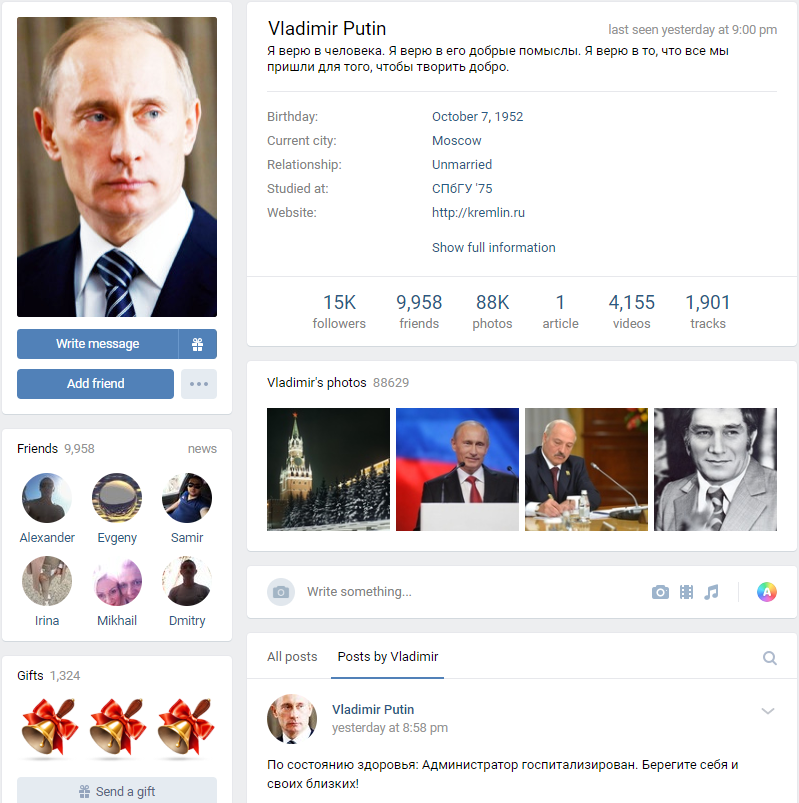
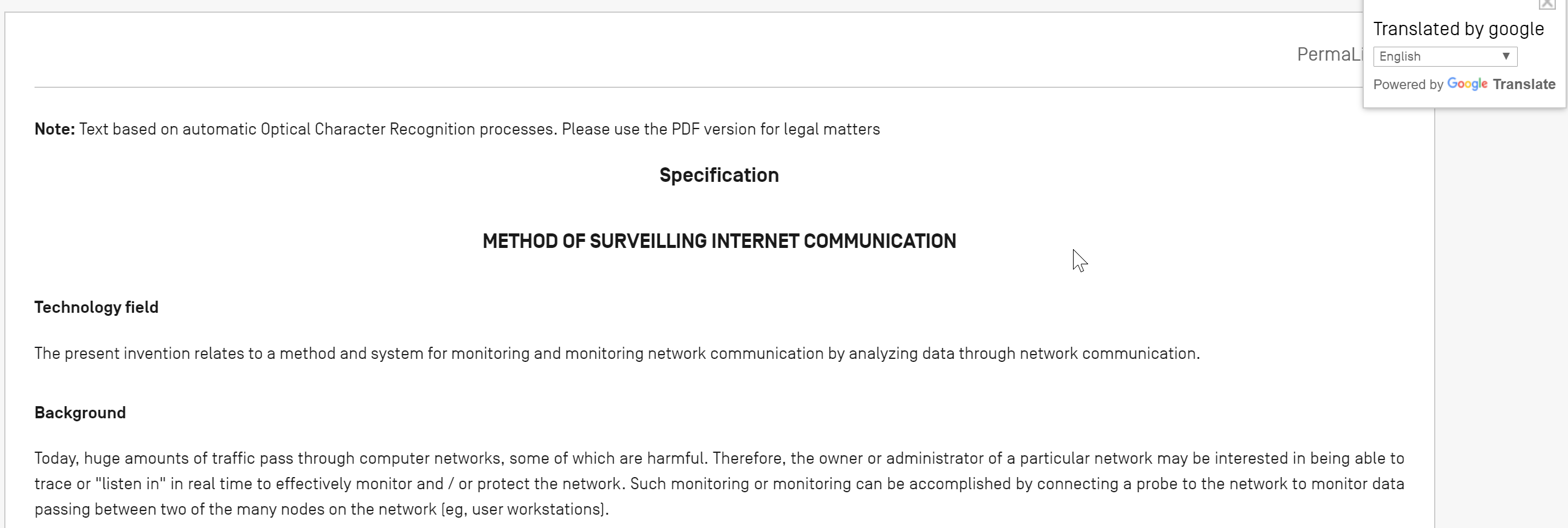
Martin recently joined Twitter and hasn’t tweeted yet. He is following 25 accounts, has no followers of his own and something about his profile picture is odd.

Since I have created many pictures using This Person Does Not Exist, I could immediately tell that the image above was created on that site. The alignment of the eyes, the weird ears and several other glitches were a sure sign of this. My buddy Nixintel wrote a great blog on how to identify such images a while back and I highly encourage you to read it.
Next up, I had a look at the other accounts Martin choose to follow. Most of them where Russia-friendly accounts, often spreading Russian propaganda, some even known conspiracy theorists. Next to the apparent German name, Martin was following German-speaking people on Twitter. So I am pretty sure he is German-speaking as well.


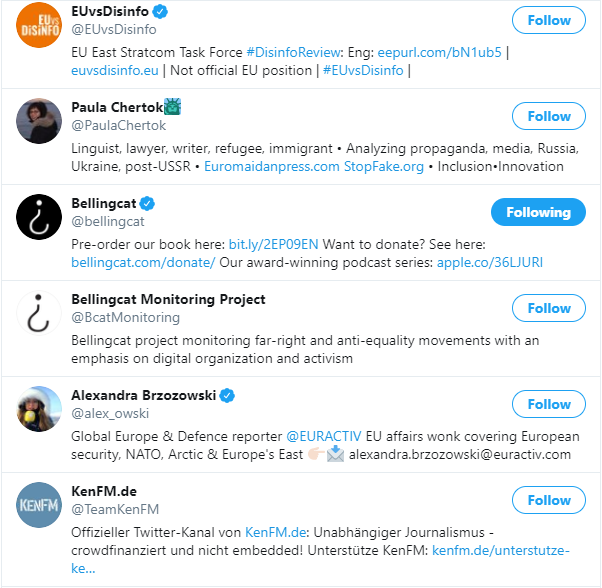
And in between all these, there where some accounts that actually investigate the general topics I mentioned above (Russia & disinformation). For me, this leaves two possibilities: Martin is either interested in the Russian propaganda and conspiracy theories from an investigative standpoint, or he supports them. It is not uncommon for supporters of conspiracy theories or foreign propaganda to follow those who try to debunk this disinformation (e.g. Bellingcat), so they can troll them. But why did he choose to follow me then, and not only me but also OSINTgeek?

OSINTgeek and I have many things in common, but none of these is any affiliation with the aforementioned topics. However, we are currently best known for organizing the German Open Source Intelligence Conference (or GOSINTCon). I could not see any interaction between Martin and the GOSINTCon Twitter account, so I decided to check our LinkedIn profile. Among the followers we received this afternoon, I found the following account:
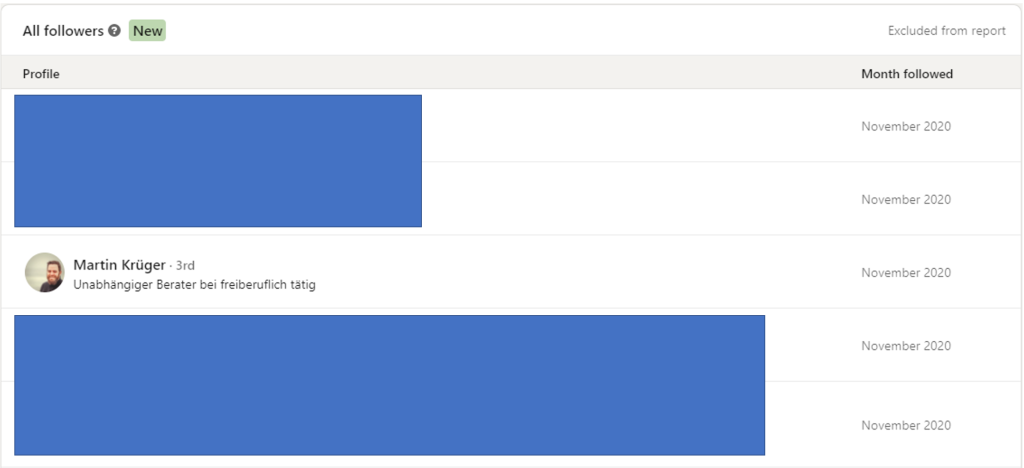
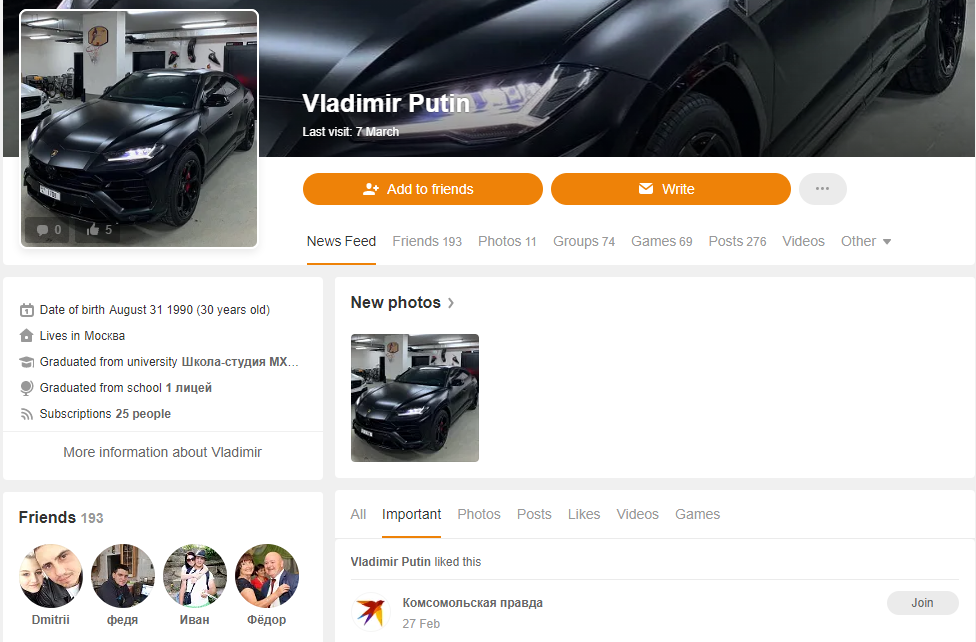
Both follows must have happened roughly around the same time. Now let’s have a look at this Martin Krüger.

Same name, different picture and also 25 connections. The picture seemed a little too good looking in my opinion. I ran a quick reverse image search on the profile picture and could see it was an often used stock photo. This was so obvious, that even Google found it!

The fact that this profile only had 25 connections, led to the assumption that it was recently created. Looking into the CV posted on LinkedIn I saw several other things that caught my eye.

I googled the name in connection with the mentioned employers and came up completely empty handed. The CV shown here also had some inconsistencies. Large gaps between apparent jobs, and to me it looked like someone just quickly and very sloppily punched something into to LinkedIn here with a mix of German and English.
All in all, both profiles seem to be sock puppets in my opinion. I thought about if I should write this up or not, as there is a very slight chance that Martin does exist. However, the name is quite common in Germany and nothing shown here can be considered as doxxing. So, this goes out to Martin:
If you are real, you might want to clean up your LinkedIn profile. Those inexplicable gaps in your CV certainly will not help your career. If you are indeed a sock puppet: gotcha! You might want to read about how to set up a proper sock puppet on the OSINT curious site or another example of how not to do so on my blog. And while sock puppets are not a topic in this year’s GOSINTCon, come back next year and we might have a talk on that.
MW-OSINT / 16.11.2020